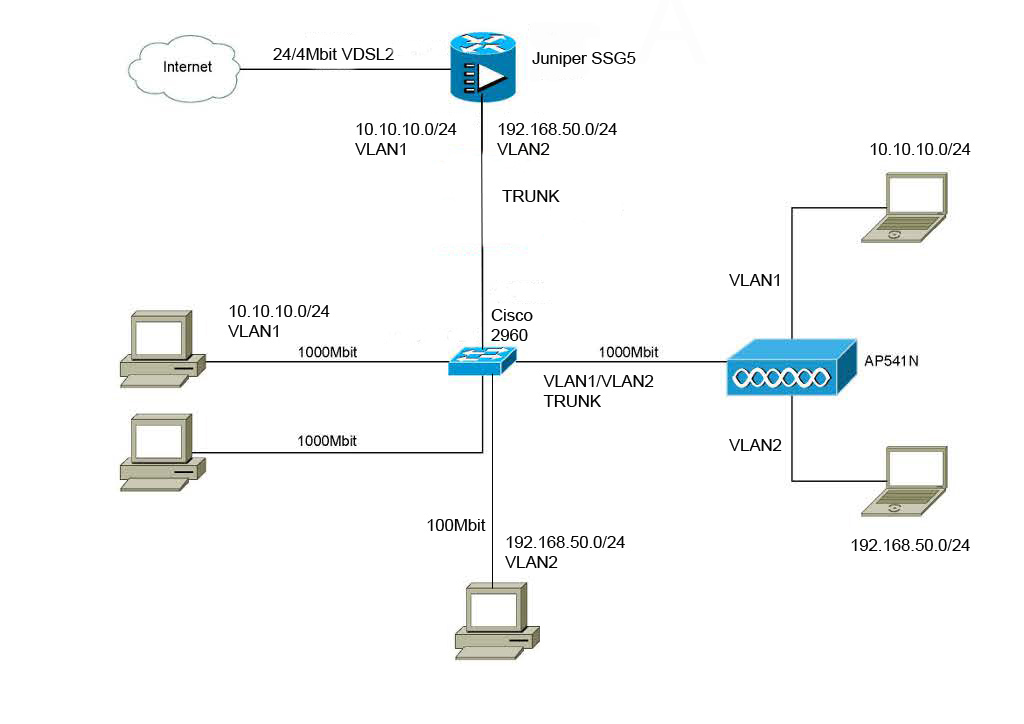
Does anyone know how a VLAN works? I have a wireless access point (Cisco WAP4410N) that is connected to a Netgear GS108E switch (will pass VLAN traffic) which is finally connected to a Netgear FVS318G firewall. I also have a wired network connected to the firewall ports.
I know the wireless access point that is creating the VLANs adds bits to the packets that identify which VLAN they go to, but what keeps any of the VLANs from seeing the wired network? How does that work? What keeps the wired network secure? Does the wired portion of the network reside on one of the VLANs?
Does it make a difference if the wired portion of the network is connected to the switch or the firewall in terms of security?
I know the wireless access point that is creating the VLANs adds bits to the packets that identify which VLAN they go to, but what keeps any of the VLANs from seeing the wired network? How does that work? What keeps the wired network secure? Does the wired portion of the network reside on one of the VLANs?
Does it make a difference if the wired portion of the network is connected to the switch or the firewall in terms of security?